Lecture
For programming microcomputers based on the MP of the KR580 kit, 244 commands are used. Below, only a part of the commands necessary for programming simple tasks will be considered. Tables of commands and brief explanations of them can be found in many sources.
It should be remembered that any machine command is a binary code word of a certain length. However, it is extremely difficult for humans to use binary codes when programming, therefore they use an assembly language or just an assembler for programming . In this language, instead of code combinations, the mnemonic form of recording operations performed in the LSI is used. Each command in assembly language corresponds to one command in the language of code combinations. Below will be considered commands in assembly language.
Before execution, the program must be translated into the language of code combinations and placed in the memory of the microcomputer. Such a translation is made automatically by a special program called an assembler. If the assembler is absent, then before entering the program such translation is done manually. In this case, the input commands in the microcomputer is usually in hexadecimal number system.
All teams MP KR580 it is advisable to divide into groups, for example, as follows:
· Forwarding single-byte exchange of operands and results between the accumulator, RON, memory, registers PPU.
· Two-byte transfer for exchanging addresses, operands, results between SPs, register pairs, memory cell pairs, stack.
· Operations in the battery, which are divided into arithmetic, logical (in the battery and the register of flags), shifts.
· Arithmetic operations in RON and memory.
· Management teams.
Commands of this group do not change the contents of the register of attributes of the РгП (F) The principles of their implementation are illustrated in Fig. 17.1.
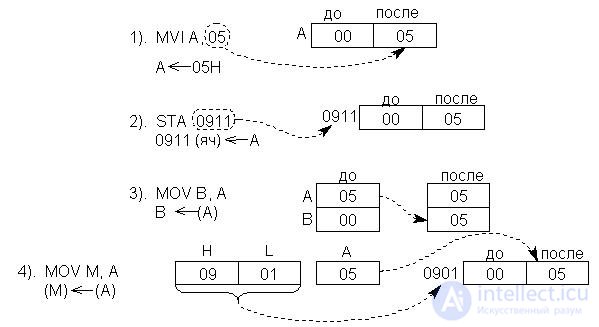
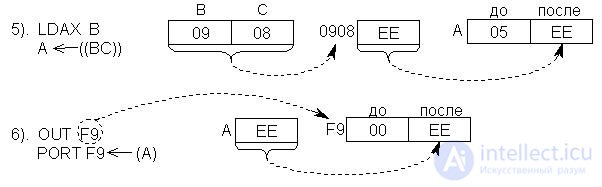
Below we consider as an example a sequence of several single-byte transfer commands. Operands and addresses are written in hexadecimal. In addition, hereinafter, it is assumed that the battery, memory cells and registers initially (before recording) contain 00:
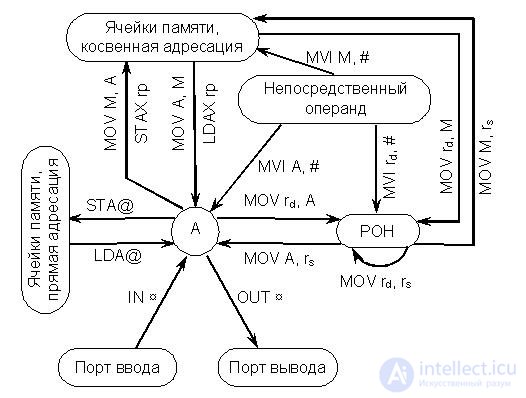

Fig.17.1. The interaction scheme of the nodes of the MP when performing single-byte transfers
The commands in this group do not change the contents of the RgP (F). The principles of their implementation are illustrated in Fig. 17.2. PSW Предп (A) (F) is assumed. 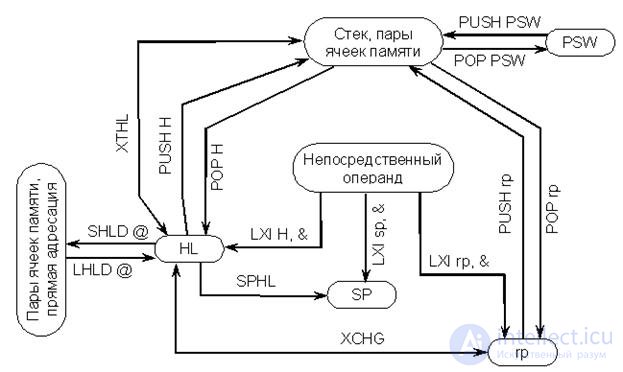
Fig.17.2. The scheme of interaction of the nodes of the MP when performing double-byte shipments; & - two-byte operand; other symbols are similar to fig. 17.1.
We explain two commands:
XCHG is the exchange of the contents of the pairs HL and DE, with (H) "(D), (L)" (E);
XTHL is the exchange of the contents of the HL pair and the top of the stack. The value of SP does not change, with (L) «((SP)) and (H)« ((SP) +1).
Consider, as an example, several double-byte transfer commands.
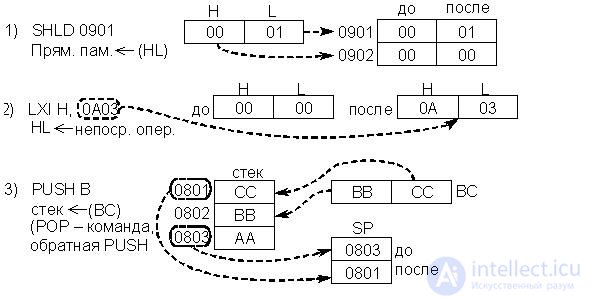

Commands of this group change the contents of the PRP (F) in accordance with the contents of the battery (Fig. 17.3).
Performed operations are divided into two-place and single .
In general, RON = AçBçCçDçEçHçL; RMS is the character code of the operation.
In turn, the two-place operations in the battery are divided into arithmetic and logical.
Double operations
· Arithmetic operations :
- the addition of the contents of the battery with the contents of the RON, memory cells (indirect addressing by HL), the immediate operand;
- the addition of the contents of the battery and the same operands and carry bits C (often denoted by CY);
- subtraction of the contents of the ROH, memory cells (indirectly addressed by HL) or the immediate operand from the contents of the battery;
- subtracting the same operands and the carry bit from the battery content;
- Comparison of the contents of the battery with the contents of the RON, memory cells (indirectly addressed by HL), the immediate operand.
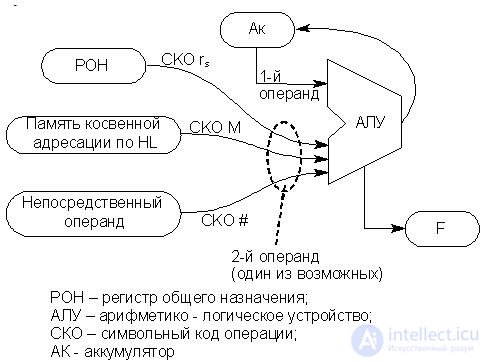
Fig.17.3. The scheme of interaction of nodes MP when performing two-place operations in the battery
In the latter case, the difference (A) - (operand) is calculated, which is not recorded anywhere (ie, A does not change), but is used to set flags in the register of attributes F.
Consider a few examples:
ADD BA ¬ (A) + (B);
SUB MA ¬ (A) - (cell (M));
ACI 07 A ¬ (A) + 07 + C;
CMP D (A) - (D) ® installation F, (A) - has not changed.
· Logical (bitwise) operations :
- the conjunction of the contents of the battery with the contents of the RHONE, a memory cell (indirectly addressed by HL), the immediate operand.
- disjunction of the contents of the battery with the contents of the RHONE, a memory cell (indirectly addressed by HL), the immediate operand.
- addition modulo 2 with the contents of the RON, a memory cell (indirectly addressed by HL), with a direct operand.
Consider a few examples:
ANA DA ¬ (A) & (D);
ANI A4 A ¬ (A) & A4;
ORA MA ¬ (A) Ú (cell (M));
XRA EA ¬ (A) Å (E);
XRI F4 A ¬ (A) Å F4.
Single operations
· Arithmetic operation :
DAA - battery decimal correction when working with binary-decimal numbers.
· Logical operations :
CMA - battery inversion;
STC - setting the C bit (ie, C ¬ 1);
CMC - Inversion of the C bit (i.e. C ¬`C).
The last two commands are executed in RSL (F).
· Shifts by 1 digit :
Examples of the implementation of shear commands are given in Fig. 17.4.
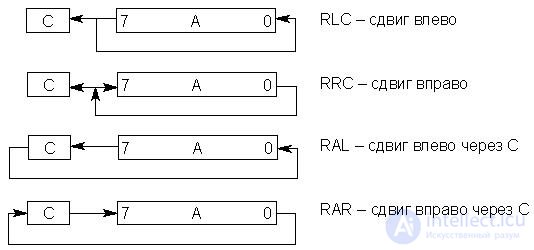
Fig.17.4. Shift operation scheme
A number of operations in the MP set of the KR580 can be performed in addition to the battery, directly in the RON and in the memory cells. These operations include:
Increment / decrement
Arithmetic single-operation operations of incrementing by 1 (increment) and decrementing by 1 (decrement) are common operations for organizing counters when viewing tables. In fig. 17.5 presents examples of the execution of these commands with RON, register pair and memory cell, indirectly addressed by HL.
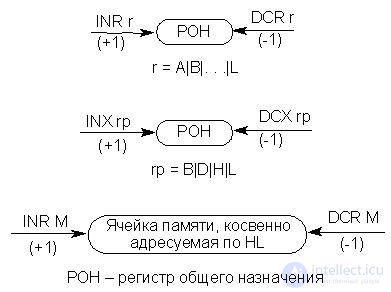
Fig.17.5. Increment / decrement
Consider two examples:
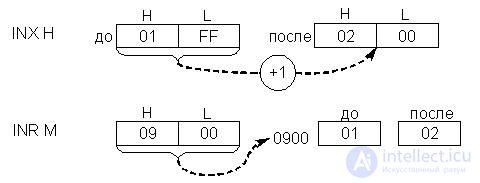
It should be remembered that with increment / decrement of the register pair, the contents are treated as a single 16-bit number. When you run this command, the transient log does not change When executing the RON increment / decrement command and memory cells indirectly addressed by HL, the PRP is changed.
Adding two-byte operands
DAD rp HL ¬ (HL) + (rp)
rp = BçDçHSP
In PRP, only the C (CY) trait changes.
The commands in this group do not change the contents of the RgP (F).
Unconditional Jump Commands
Direct address
JMP @, where @ is a two-byte address (@ ® PC).
For example:
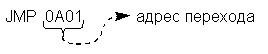
By indirect address
PCHL - the address of the transition is stored in the register pair HL. When it is executed (HL) → PC.
Conditional jump commands
Jcon @, where con is the condition mnemonic from the English word condition.
Earlier it was noted that as a condition for the transition, the state of the bits (flags) of the RGF (F) is used. The mnemonics corresponding to these states are shown in fig. 17.6.
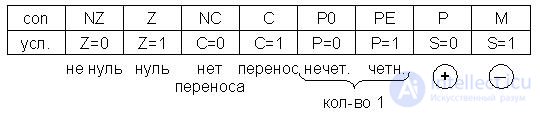
Fig.17.6. Register of attributes РгП (F)
For example: JC 8BFE - with C = 1, the transition at the address 8BFE, with C = 0, the next command is executed at the address.
Commands call PP and return
Earlier it was noted that the return address is automatically saved in the stack, i.e. (PC) ® stack.
Unconditional commands
CALL @ - subroutine call;
RET - return from subroutine.
Conditional commands
Ccon @ - subroutine call;
Rcon - return from subroutine.
The action of the commands is similar to the action of conditional transition commands, if the condition is true, then call or return. If not, the following commands are executed.
Other control commands
RST n, where n = 0,1, ..., 7 - restart on interrupt vector n.
When executing this command, control is transferred to the subroutine servicing the interrupt. During the execution of the RST command, the contents of the PC command counter are stored in the stack, and the address of the corresponding interrupt vector is written to the PC.
This address is set as follows. The RST command has the structure 11NN N111, i.e. one byte The three-digit combination NNN is specified by the value n (n = 0 ... 7). The value of 0000 0000 00NN N000 is entered in the PC command counter, which serves as the address of the corresponding interrupt vector.
Thus, by setting a certain value n, you can form the address of one of the eight interrupt vectors. These addresses are located in the zone from 0000H to 0038H of the address space and go through 8 bytes, i.e. the first 64 memory cells are reserved for them (each of the 8 vectors is allocated 8 bytes). In these zones (8 bytes), only the transition commands to the corresponding subroutines (handlers), which are located in other memory areas, are written.
Interrupting subprograms (like regular subprograms) must end with the RET command. During the execution of this command, the address of the command of the main program, before which the interruption occurred, is selected from the stack and transferred to the RA address register, and the value increased by 1 is entered into the command counter.
EI - enable interrupts. This command is placed at the beginning of the program section on which the interrupt is enabled. At this command, the interrupt enable trigger in the CU MP is set to state 1.
DI - interrupt prohibition. This command is placed at the end of the program section in which the interrupt was enabled, and resets the trigger to the state 0.
NOP is an "empty" command. Performs four clock cycles. Only the PC changes.
HLT - stop. Causes program termination and going into a stop state. The MP is disconnected from the external address and data buses (i.e., their buffers go to the Z state). At the output WAIT (standby) is set to level 1. This state can be interrupted by triggering the MP or by transferring it to the interrupt state.
1. Schemes of interaction of MP KP580VM80 nodes when performing one-and two-byte transfers.
2. The scheme of interaction of MP KP580VM80 nodes when performing two-place operations in the battery.
3. Types of shift operations and their execution.
4. Management teams in MP KR580VM80.
Comments
To leave a comment
Computer circuitry and computer architecture
Terms: Computer circuitry and computer architecture