Lecture
Fraud (fraud — fraud) in cellular mobile communication systems is an activity aimed at using cellular services without paying them properly. Fraud is found in all areas of human activity, unfortunately. But a feature of fraud in cellular mobile communication systems is that the use of radio channels in the sections from the mobile to the base station to a certain extent facilitates access, namely unauthorized access, to the radio channel (perhaps even imperceptible). Therefore, the temptation to use such opportunities scams is very large, and at the same time as the development of cellular mobile communication systems, methods and techniques of fraud are developed. The forms in which fraud manifests itself are extremely diverse [8.1-8.9]. Below we consider several basic forms of fraud [8.3].
Subscription fraud.
Subscription fraud (subscription fraud) is reduced to malicious defaults with intensive use of a mobile phone. For example, a cellular network client during the reporting period (from payment to payment - a month) after registering a mobile phone and subscribing to cellular services provided by the operator, heavily uses airtime (even reselling it to other users) for long-distance and international calls. After the reporting time, the subscriber simply disappears, moving away from the payment. If the operator company closely monitors the airtime consumed by subscribers, then especially the fraud client will behave with restraint, but then in the second (or third) month (before disappearing) it can activate the use of airtime. Fraud clients, in addition to the usual non-payment and disappearance, actively use such circumstances as the sale of subscriber units on credit, seasonal population migration (for example, the summer holiday season), etc.
Possible measures to combat subscription fraud:
- obtaining sufficiently complete information about new users, their creditworthiness when selling MS and entering into an agreement with the operator;
- operational exchange of operator companies with MS-dealers and other companies;
- tracking by the operator of the expenditure of airtime, the number of user negotiations, up to the introduction of restrictions on the time of use of channels;
- the introduction of relevant articles in the law on telecommunications.
Technical fraud.
Technical fraud is one of the most diverse, extensive and evolving fraud forms. The share of technical fraud accounts for 60 ... 70% of the revenue loss of cellular operators in developed countries of the world.
There are several examples that make it possible to assess the level of this kind of fraud.
- Turbing - alteration of electronic serial numbers in mobile phones. This fraud was typical of analog cellular standards with their simple authentication. The essence of the fraud was that MS worked out such that on each subsequent call MS transmitted a new electronic serial number, that is, the called subscriber was perceived in the MSC switching center as a new roamer, which received the possibility of conducting a conversation without a full check and, of course, without further payment.
- Cloning (vegetative propagation) - cloning or the process of “cellular counterparts”, that is, MSi is supplemented with MS2, while the same numbers — passwords (for example, MSi subscriber's ID) are used for authentication in the duplicate MS2 MSb and the owner of the main MSi pays for calls from the backup MS2 device.
The main and rather difficult task is to obtain information about the number-passwords of the devices of actual subscribers. In addition to the "agent" methods (purchase or theft from suppliers or dealers), special complex scanners are used (scanning receivers). The sophistication of the fraud business is currently developing in the direction of creating unique scanning receivers that not only implement fraud, but also highlight information on telephone conversations of subscribers.
Illegal mobile stations such as clones.
MS used for commercial communications, for example, to sell expensive international calls. The scheme of this type of fraud may be as follows:
- one of the participants of the fraud operation from the payphone of the “international telephone communication” from an ordinary telephone set causes an illegal clone-cellular device MS2 of the fraud partner and sets him the task of organizing a conference call;
- fraud partner from the clone mobile device MS2 calls the desired foreign subscriber and organizes a conference call, that is, a joint telephone conversation between three subscribers: the fraud subscriber on a standard telephone set, the foreign subscriber (on MS), the subscriber on the clone is MS2.
As a result, the fraud subscriber - the customer holds the communication session he needs, and the payment is charged to the account of the actual owner of the used mobile number MSi.
Theft of subscriber devices.
Thefts of subscriber devices (thefts) are detrimental not only to users, but also to operator companies, since after using these MSs there is an additional stream of unpaid calls. In this case, the sooner the user informs the operator about the theft, the sooner the operator will block the stolen MS and the less will be the financial losses of the user and the operator. The share of losses from MS thefts is relatively small, but tends to increase. In fig. 8.1 shows a graph of losses due to theft, subscription fraud and total losses by year in millions of dollars in the United States. In 1996, in the United States, 5% of the revenues of cellular operators were lost due to fraud (which amounted to $ 1.080 billion, with a total income of $ 21 billion).
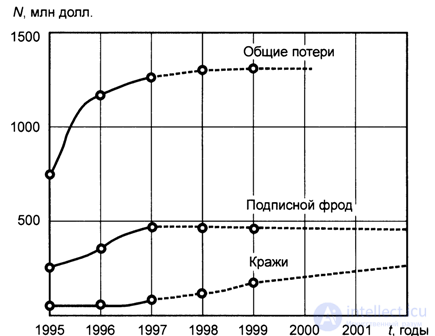
Fig. 8.1. Absolute loss from fraud [8.3] (US, data from the Yankee Group)
Anti-fraud measures
At present, on the one hand, fraud participants, on the one hand, and equipment manufacturers and cellular mobile communication system operators, on the other, are in continuous struggle, which does not bring complete victory to either side, but allows them to maintain dynamic equilibrium.
With technical fraud and specifically with MS cloning, the fight is implemented by introducing an improved authentication procedure, which is conveniently implemented in digital standards, including GSM. Extraction of information necessary for cloning from radio is practically impossible in digital systems. The “radio frequency fingerprints” method - RF (Radio Frequency) finger-printing is quite promising, in which for each subscriber's device such subtle characteristics as small (within tolerances) deviations from the nominal frequency used, parameters modulation, etc. The implementation of this method is technically difficult, but the probability of supporting such a radio-frequency "portrait" is extremely small. It is possible to use MS voice recognition systems, sets of restrictions on call time and location of specific subscribers, etc.
To combat subscription fraud, they use control over MS sales points, check subscribers' creditworthiness, etc. The operational exchange between operator companies and between different companies, for example, in connection with the development of roaming, is especially important. The GSM MoU Association recommended, in particular, that information be exchanged between roaming operators within 36 hours.
Prompt exchange of information is very important in combating the use of stolen or ^ certified MS. The GSM standard for this purpose provides for the presence in each cellular network of a corresponding database - the EIR register, and at the headquarters of the GSM MoU association in Dublin (Ireland) a global database is created - the Central Equipment Identity Register — CEIR {Central EIR). successful countering fraud have the development and adoption of appropriate legislation, and the laws must be quite versatile and effective, taking into account the high rates of development of both mobile communications and types of fraud.
In the United States, Section 18 of the Code of Federal Laws - the United States Code (USC) - contains the following articles related to mobile communication systems:
- article 1028 - fraudulent use of identification;
- Article 1029 - fraudulent use of access devices;
- Article 1030 - fraudulent use of computers.
Article 1029, as amended, is entitled “Frode and related activities in combination with access devices”. It establishes, among other things, penalties in the form of fines and / or imprisonment for a term of up to 10 ... 20 years for fraud in the field of telecommunications, in particular for intentional and fraud use, production, possession or storage of appropriately modified equipment and scanning devices. receivers, as well as devices or software used to improve telecommunication equipment in order to gain unauthorized access to telecommunication services. ”
In the GSM MoU, a separate working group deals with fraud issues.
Comments
To leave a comment
GSM Basics
Terms: GSM Basics