Lecture
In the TCP / IP stack, the TCP (Transmission Control Protocol) protocol works the same as the UDP protocol at the transport layer. It provides reliable data transport between application processes by establishing a logical connection.
The unit of TCP data is a segment. Information arriving at the TCP protocol within a logical connection from higher level protocols is considered by TCP as an unstructured stream of bytes. Incoming data is buffered by TCP. For transmission to the network layer from the buffer "cut" some continuous part of the data, called a segment.
TCP provides for the case when an application requests an urgent data transfer (PSH bit in the request is set to 1). In this case, TCP, without waiting for the buffer to fill the segment size, immediately sends the specified data to the network. Such data is said to be transmitted out of band.
Not all segments sent through a connection will be of the same size, but both participants in the connection must agree on the maximum size of the segment that they will use. This size is chosen in such a way that when a segment is packed into an IP packet, it is placed there entirely, that is, the maximum segment size must not exceed the maximum size of the IP packet data field. Otherwise, it would be necessary to perform fragmentation, that is, to divide the segment into several parts, in order to fit it into an IP packet.
Similar problems are solved at the network level. In order to avoid fragmentation, an appropriate maximum IP packet size must be selected. However, this should take into account the maximum size of the frame data field (MTU) of all data link layer protocols used in the network. The maximum segment size must not exceed the minimum value on the set of all MTUs of the composite network.
In TCP as well as in UDP, ports are used for communication with application processes. Port numbers are assigned in the same way: there are standard, reserved numbers (for example, number 21 is assigned to the FTP service, 23 to telnet), and less well-known applications use arbitrarily chosen local numbers.
However, TCP uses ports in a slightly different way. For the organization of reliable data transfer provides for the establishment of a logical connection between the two application processes. Within the connection, a mandatory acknowledgment of the correctness of reception for all transmitted messages is made, and if necessary, a retransmission is performed. A TCP connection allows you to transfer data simultaneously in both directions, that is, full duplex transmission.
A TCP connection is identified by a pair of full addresses of both interacting processes (endpoints). The address of each of the endpoints includes the IP address (network number and computer number) and port number. One endpoint can participate in multiple connections.
Connection establishment is performed in the following sequence:
As part of the connection, the correctness of the transfer of each segment must be confirmed by the receipt of the recipient. Handshaking is one of the traditional methods of ensuring reliable communication. The idea of handshaking is as follows.
In order to be able to organize the re-transmission of corrupted data, the sender numbers the sent units of transmitted data (hereinafter referred to as frames for simplicity). For each frame, the sender expects a so-called positive receipt from the receiver - a service message informing that the original frame was received and the data in it was correct. This waiting time is limited - when sending each frame, the transmitter starts a timer, and if after its expiration a positive receipt is not received, then the frame is considered lost. In some protocols, the receiver, in case of receiving a frame with corrupted data, must send a negative receipt - an explicit indication that the frame must be retransmitted.
There are two approaches to the organization of the exchange of positive and negative receipts: with downtime and with the organization of the "window".
The method with idle times requires that the source who sent the frame expect to receive a receipt (positive or negative) from the receiver and only after that send the next frame (or repeat the distorted one). From Figure 6.1 it can be seen that in this case the performance of data exchange is significantly reduced - although the transmitter could have sent the next frame immediately after sending the previous one, it must wait for the receipt of the receipt. The decline in performance for this correction method is especially noticeable on low-speed communication channels, that is, in territorial networks.
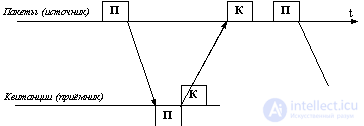
Fig. 6.1. Method of confirming the correct transmission of frames with idle source
In the second method, to increase the line utilization rate, the source is allowed to transmit a certain number of frames in a continuous mode, that is, at the maximum possible rate for the source, without receiving response tickets for these frames. The number of frames allowed to transmit in this manner is called the window size. Figure 6.2 illustrates this method for window size in W frames. Usually, the frames in the exchange are numbered cyclically, from 1 to W. When sending a frame with number 1, the source is allowed to transmit another W-1 frame before receiving a receipt for frame 1. If during this time the receipt for frame 1 has not arrived, then the transfer process pauses, and after a certain timeout, frame 1 is considered lost (or the receipt for it is lost) and it is transmitted again.
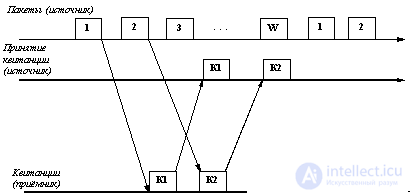
Fig. 6.2. The method of "window" - continuous sending packets
If the receipt stream arrives more or less regularly, within the tolerance of W frames, the exchange rate reaches the maximum possible value for the given channel and the received protocol.
This algorithm is called the sliding window algorithm. Indeed, every time a receipt is received, the window moves (slides), capturing new data that is allowed to be transmitted without confirmation.
TCP implements a form of acknowledgment algorithm using a window. A feature of this algorithm is that, although the unit of data to be transmitted is a segment, the window is defined on the set of numbered bytes of an unstructured data stream coming from the upper layer and buffered by the TCP protocol.
The receipt is sent only if the data is received correctly, negative receipts are not sent. Thus, the absence of a receipt means either the reception of a distorted segment, or the loss of a segment, or the loss of a receipt.
As a receipt, the recipient of the segment sends a response message (segment) in which it places a number that is one greater than the maximum byte number in the received segment. If the window size is W, and the last receipt contained the value of N, then the sender can send new segments until the next segment has a byte with the number N + W. This segment goes beyond the window, and the transmission in this case must be suspended until the next receipt arrives.
The choice of waiting time (time-out) for the next receipt is an important task, the result of which affects the performance of the TCP protocol.
The time-out should not be too short, in order to eliminate redundant re-transmissions as far as possible, which reduces the useful system capacity. But it should not be too large to avoid lengthy downtime associated with the expectation of a nonexistent or "lost" receipt.
When choosing the time-out value, the speed and reliability of physical communication lines, their length and many other similar factors should be taken into account. In TCP, the timeout is determined using a rather complex adaptive algorithm, the idea of which is as follows. At each transmission, the time from the moment of sending a segment to the arrival of a receipt for its acceptance (turnover time) is recorded. The resulting values of turnover times are averaged with weighting coefficients increasing from the previous measurement to the subsequent one. This is done in order to increase the influence of recent measurements. The average time of turnover multiplied by a certain coefficient is chosen as a time-out. Practice shows that the value of this coefficient should exceed 2. In networks with a large scatter of turnaround time, when choosing a time-out, the dispersion of this quantity is also taken into account.
By varying the size of the window, you can affect the network load. The larger the window, the larger the portion of unacknowledged data that can be sent to the network. If the network does not cope with the load, then there are queues at intermediate nodes, routers and end nodes of computers.
When the receiving node's overflow buffer overflows, the "overloaded" TCP protocol, sending a receipt, places a new, reduced window size into it. If he completely refuses to receive, then a zero-size window is indicated in the receipt. However, even after that, the application can send a message to the refused port. To do this, the message must be marked "urgent" (the URG bit in the request is set to 1). In such a situation, the port is obliged to accept a segment, even if for this it is necessary to force out the data already there.
After receiving the receipt with the zero value of the protocol-sender window, from time to time makes a control attempt to continue data exchange. If the receiving protocol is already ready to receive information, then in response to a control request, it sends a receipt indicating the non-zero size of the window.
Another manifestation of network congestion is buffer overflow in routers. In such cases, they can centrally resize the window by sending control messages to some end nodes, which allows them to differentiate the flow of data in different parts of the network.
TCP messages are called segments and consist of a header and a block of data. The segment header has the following fields:
Comments
To leave a comment
Computer networks
Terms: Computer networks