Lecture
Steganography (from the Greek. Στεγανός - hidden + γράφω - I write; literally “secret writing”) is the science of the hidden transmission of information by keeping the fact of transmission itself secret. This term was introduced in 1499 by Johann Trithemius in his treatise "Steganography" ( Steganographia ), encrypted under a magic book.
Unlike cryptography, which hides the contents of a secret message, steganography hides the very fact of its existence. Typically, the message will look like anything else, such as an image, article, shopping list, letter, or sudoku. Steganography is usually used in conjunction with cryptography methods, thus complementing it.
The advantage of steganography over pure cryptography is that messages do not attract attention. Messages whose encryption is not hidden are suspicious and may themselves be incriminating in those countries in which cryptography is prohibited . Thus, cryptography protects the content of the message, and steganography protects the very fact that there are any hidden messages.
The first record on the use of steganography is found in the treatise of Herodotus “History”, referring to 440 BC. e. The treatise described two methods for hiding information. DeMarat sent a warning about the upcoming attack on Greece, writing it down on the wooden backing of a wax tablet before waxing. The second method was as follows: the necessary message was written to the shaved head of the slave, and when his hair grew, he went to the addressee, who shaved his head again and read the delivered message.
There is a version that the ancient Sumerians were among the first to use steganography , since many clay cuneiform tablets were found in which one record was covered with a layer of clay, and another was written on the second layer. However, opponents of this version believe that it was not at all an attempt to hide information, but merely a practical need.
In the late 90s, several areas of steganography were distinguished:
One of the most common methods of classical steganography is the use of sympathetic (invisible) ink. Text written with such ink appears only under certain conditions (heating, lighting, chemical developer, etc.) [7] Invented as early as the 1st century AD er Philo of Alexandria [8], they continued to be used both in the Middle Ages and in modern times, for example, in letters from Russian revolutionaries from prisons. In Soviet times, schoolchildren in literature classes studied the story, as Vladimir Lenin wrote with milk on paper between the lines (see Tales of Lenin). Milk strings became visible when heated above a candle flame.
There is also an ink with a chemically unstable pigment. What is written with this ink looks like what is written with a regular pen, but after a certain time the unstable pigment decomposes, and there is not a trace of the text. Although when using a standard ballpoint pen, text can be restored by the deformation of the paper, this disadvantage can be eliminated by using a soft writing unit, like a felt-tip pen.
During the Second World War, microdots were actively used - microscopic photographs glued into the text of letters.
There are also a number of alternative methods for hiding information: [7]
Currently, steganography is most often understood as hiding information in text, graphic, or audio files using special software.
Steganographic models - used for a general description of steganographic systems.
In 1983, Simmons proposed the so-called. "The problem of prisoners." Its essence is that there is a man in freedom (Alice), imprisoned (Bob) and guard Willie. Alice wants to send messages to Bob without the intervention of a security guard. In this model, some assumptions are made: it is assumed that, before the conclusion, Alice and Bob agree on a code symbol that will separate one part of the text of the letter from the other in which the message is hidden. Willy also has the right to read and modify messages. In 1996, a unified terminology was adopted at the Information Hiding: First Information Workshop conference:
Computer steganography - the direction of classical steganography, based on the features of a computer platform. Examples are the steganographic file system StegFS for Linux, hiding data in unused areas of file formats, substitution of characters in file names, textual steganography, etc. Let us give some examples:

The image of a tree with another image hidden by digital steganography in it. The image is hidden by removing all but two lower bits from each color component and subsequent normalization.

The image of a cat, extracted from the image of the tree above
Digital steganography - the direction of classical steganography, based on the concealment or the introduction of additional information into digital objects, while causing some distortion of these objects. But, as a rule, these objects are multimedia objects (images, video, audio, textures of 3D objects) and making distortions that are below the sensitivity threshold of an average person does not lead to noticeable changes to these objects. In addition, in digitized objects that are initially analog in nature, there is always quantization noise; Further, when these objects are reproduced, additional analog noise and nonlinear distortions of the equipment appear, all of which contribute to the greater invisibility of the hidden information.
Recently, methods have gained popularity when hidden information is transmitted through computer networks using the features of data transfer protocols. Such methods are called network steganography. This term was first introduced by Krzysztof Szpierski (Polish. Krzysztof Szczypiorski ) in 2003. Typical methods for network steganography include changing the properties of one of the network protocols. In addition, interconnection between two or more different protocols can be used in order to more securely conceal the transmission of a secret message. Network steganography covers a wide range of methods, in particular:
The principle of operation of the LACK is as follows. The transmitter (Alice) selects one of the voice stream packets, and its payload is replaced by the bits of the secret message — a steganogram that is embedded in one of the packets. Then the selected package is intentionally delayed. Every time an excessively delayed packet reaches a recipient unfamiliar with the steganographic procedure, he is discarded. However, if the recipient (Bob) is aware of the hidden connection, then instead of deleting the received RTP packets, it extracts the hidden information [9].
All embedded information embedding algorithms can be divided into several subgroups:
According to the method of embedding information, the algorithms can be divided into linear (additive), nonlinear, and others. Algorithms for additive information injection consist in a linear modification of the original image, and its extraction in the decoder is performed by correlation methods. In this case, the CEH is usually folded with a container image, or is “fusion” (fusion) into it. In nonlinear methods of embedding information, scalar or vector quantization is used. Among other methods, methods using the ideas of fractal image coding are of particular interest. The additive algorithms include:
LSB method
LSB (Least Significant Bit, the least significant bit) - the essence of this method is to replace the last significant bits in the container (image, audio or video) with the bits of the message to be hidden. The difference between empty and filled containers should not be perceptible to human organs.
The essence of the method is as follows: Suppose there is an 8-bit image in grayscale. 00h (00000000b) indicates black color, FFh (11111111b) - white. There are a total of 256 gradations ( 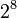 ). Also assume that the message consists of 1 byte - for example, 01101011b. When using 2 lower bits in pixel descriptions, we will need 4 pixels. Suppose they are black. Then the pixels containing the hidden message will look like this: 00000001 00000010 00000010 00000011. Then the color of the pixels will change: the first - on 1/255, the second and third - on 2/255 and the fourth - on 3/255. Such gradations, not only that imperceptible to humans, may not appear at all when using low-quality output devices.
). Also assume that the message consists of 1 byte - for example, 01101011b. When using 2 lower bits in pixel descriptions, we will need 4 pixels. Suppose they are black. Then the pixels containing the hidden message will look like this: 00000001 00000010 00000010 00000011. Then the color of the pixels will change: the first - on 1/255, the second and third - on 2/255 and the fourth - on 3/255. Such gradations, not only that imperceptible to humans, may not appear at all when using low-quality output devices.
LSB methods are unstable to all types of attacks and can be used only in the absence of noise in the data transmission channel.
The LSB-encoded stego is detected by the anomalous characteristics of the distribution of the values of the low bits of the digital signal samples.
All LSB methods are usually additive (A17, L18D).
Other methods of hiding information in graphic files are focused on lossy file formats, for example, JPEG. Unlike LSB, they are more resistant to geometric transformations. This is obtained by varying in a wide range of image quality, which makes it impossible to determine the source of the image.
Echo methods
Echo techniques are used in digital audio steganography and use uneven gaps between echoes to encode a sequence of values. When a number of restrictions are imposed, the condition of invisibility for human perception is observed. Echo is characterized by three parameters: initial amplitude, degree of attenuation, delay. When a certain threshold is reached between the signal and the echo, they mix. At this point, the human ear can no longer distinguish these two signals. The presence of this point is difficult to determine, and it depends on the quality of the original recording, the listener. The most commonly used delay is about 1/1000, which is quite acceptable for most recordings and listeners. Two different delays are used to indicate a logical zero and one. Both of them should be less than the threshold of sensitivity of the listener's ear to the received echo.
Echo methods are resistant to amplitude and frequency attacks, but unstable against time attacks.
Phase encoding
Phase coding (phase coding, phase coding) - also used in digital audio stereography. The original sound element is replaced with a relative phase, which is the secret message. The phase of successive elements should be added in such a way as to preserve the relative phase between the original elements. Phase encoding is one of the most effective methods to hide information.
Spread spectrum method
The method of embedding a message is that a special random sequence is embedded in the container, then, using a matched filter, this sequence is detected. This method allows you to embed a large number of messages in the container, and they will not interfere with each other, provided that the sequences used are orthogonal. The advantage of this method is to counteract geometric transformations, removal of part of the file, and so on. The method is borrowed from broadband.
An attack on the stegosystem is an attempt to detect, extract, change a hidden steganographic message. Такие атаки называютсястегоанализом по аналогии с криптоанализом для криптографии. Способность стеганографической системы противостоять атакам называетсястеганографической стойкостью. Наиболее простая атака — субъективная. Внимательно рассматривается изображение, прослушивается звукозапись в попытках найти признаки существования в нём скрытого сообщения. Такая атака имеет успех лишь для совсем незащищенных стегосистем. Обычно это первый этап при вскрытии стегосистемы. Выделяются следующие типы атак.[10]
Рассмотрим некоторые из них:
Атака по известному заполненному контейнеру — у взломщика имеется одно или несколько стего. В случае нескольких стего считается, что запись скрытой информации проводилось отправителем одинаковым способом. Задача взломщика заключается в обнаружении факта наличия стегоканала, а также доступа к нему или определения ключа. Имея ключ, можно раскрыть другие стегосообщения.
Атака по известной математической модели контейнера — взломщик определяет отличие подозрительного послания от известной ему модели. К примеру, пусть биты внутри отсчета изображения коррелированны. Тогда отсутствие корреляции может служить сигналом о наличии скрытого сообщения. При этом задача внедряющего сообщение состоит в том, чтобы не нарушить статистических закономерностей в контейнере.
Атака на основе известного пустого контейнера — если злоумышленнику известен пустой контейнер, то сравнивая его с предполагаемым стего можно установить наличие стегоканала. Несмотря на кажущуюся простоту метода, существует теоретическое обоснование эффективности этого метода. Особый интерес представляет случай, когда контейнер нам известен с некоторой погрешностью (такое возможно при добавлении к нему шума).
Цифровые водяные знаки (ЦВЗ) используются для защиты от копирования, сохранения авторских прав. Невидимые водяные знаки считываются специальным устройством, которое может подтвердить либо опровергнуть корректность. ЦВЗ могут содержать различные данные: авторские права, идентификационный номер, управляющую информацию. Наиболее удобными для защиты с помощью ЦВЗ являются неподвижные изображения, аудио и видео файлы.
Технология записи идентификационных номеров производителей очень похожа на ЦВЗ, но отличие состоит в том, что на каждое изделие записывается свой индивидуальный номер (так называемые «отпечатки пальцев»), по которому можно вычислить дальнейшую судьбу изделия. Невидимое встраивание заголовков иногда используется, к примеру, для подписей медицинских снимков, нанесения пути на карту и т. п. Скорее всего, это единственное направление стеганографии, где нет нарушителя в явном виде.
Основные требования, предъявляемые к водяным знакам: надёжность и устойчивость к искажениям, незаметности, робастности к обработке сигналов (робастность — способность системы к восстановлению после воздействия на неё внешних/внутренних искажений, в том числе умышленных). ЦВЗ имеют небольшой объём, но для выполнения указанных выше требований, при их встраивании используются более сложные методы, чем для встраивания обычных заголовков или сообщений. Такие задачи выполняют специальные стегосистемы.
Перед помещением ЦВЗ в контейнер, водяной знак нужно преобразовать к подходящему виду. К примеру, если в качестве контейнера используется изображение, то и ЦВЗ должны быть представлена как двумерный битовый массив.
Для повышения устойчивости к искажениям часто применяют помехоустойчивое кодирование или используют широкополосные сигналы. Начальную обработку скрытого сообщения делает прекодер. Важная предварительная обработка ЦВЗ — вычисление его обобщенного Фурье-преобразования. Это повышает помехоустойчивость. Первичную обработку часто производят с использованием ключа — для повышения секретности. Потом водяной знак «укладывается» в контейнер (например, путем изменения младших значащих бит). Здесь используются особенности восприятия изображений человеком. Широко известно, что изображения имеют огромную психовизуальную избыточность. Глаза человека подобны низкочастотному фильтру, который пропускает мелкие элементы изображения. Наименее заметны искажения в высокочастотной области изображений. Внедрение ЦВЗ также должно учитывать свойства восприятия человека.
Во многих стегосистемах для записи и считывания ЦВЗ используется ключ. Он может предназначаться для ограниченного круга пользователей или же быть секретным. Например, ключ нужен в DVD-плейерах для возможности прочтения ими содержащихся на дисках ЦВЗ. Как известно, не существует таких стегосистем, в которых бы при считывании водяного знака требовалась другая информация, нежели при его записи. В стегодетекторе происходит обнаружение ЦВЗ в защищённом им файле, который, возможно, мог быть изменён. Эти изменения могут быть связаны с воздействиями ошибок в канале связи, либо преднамеренными помехами. В большинстве моделей стегосистем сигнал-контейнер можно рассмотреть как аддитивный шум. При этом задача обнаружения и считывания стегосообщения уже не представляет сложности, но не учитывает двух факторов: неслучайности сигнала контейнера и запросов по сохранению его качества. Учет этих параметров позволит строить более качественные стегосистемы. Для обнаружения факта существования водяного знака и его считывания используются специальные устройства — стегодетекторы. Для вынесения решения о наличии или отсутствии водяного знакаиспользуют, к примеру, расстояние по Хэммингу, взаимокорреляцию между полученным сигналом и его оригиналом. В случае отсутствия исходного сигнала в дело вступают более изощренные статистические методы, которые основаны на построении моделей исследуемого класса сигналов.
Жёлтые точки
Стеганография используется в некоторых современных принтерах. При печати на каждую страницу добавляются маленькие точки, содержащие информацию о времени и дате печати, а также серийный номер принтера.[11]
Из рамок цифровой стеганографии вышло наиболее востребованное легальное направление — встраивание цифровых водяных знаков (ЦВЗ)(watermarking), являющееся основой для систем защиты авторских прав и DRM (Digital rights management) систем. Методы этого направления настроены на встраивание скрытых маркеров, устойчивых к различным преобразованиям контейнера (атакам).
Полухрупкие и хрупкие ЦВЗ используются в качестве аналоговой ЭЦП, обеспечивая хранение информации о передаваемой подписи и попытках нарушения целостности контейнера (канала передачи данных).
Например, разработки Digimarc в виде плагинов к редактору Adobe Photoshop позволяют встроить в само изображение информацию об авторе. Однако такая метка неустойчива, впрочем как и абсолютное их большинство. Программа Stirmark, разработчиком которой является ученый Fabien Petitcolas, с успехом атакует подобные системы, разрушая стеговложения.

An example showing how terrorists can use devices to send hidden messages. This picture contains the message “The boss said we should blow up the bridge at midnight.” Encrypted using http: //mozaiq.org/encrypt using the “växjö” character combination as the password.
Rumors about the use of steganography by terrorists appeared since the publication of two articles in USA Today on February 5, 2001 - “Terrorists are hiding instructions online” [12] and “Terrorist groups are hiding behind web encryption.” [13] On July 10, 2002, an article appeared in the same newspaper, “Militants envelop the web with links to jihad. This article published information that terrorists used photographs on eBay to transmit hidden messages. [14] Many media reprinted data messages, especially after the terrorist attacks of September 11, although no confirmation of this information was received. Articles in USA Today were written by a foreign correspondent, Jack Kelly, who was fired in 2004 after it turned out that this information was [15] On October 30, 2001, The New York Times published an article entitled “Disguised terrorist messages may be hiding in cyberspace.” [16] The article suggested that al-Qaeda used steganography to hide messages in images, and then transferred them to e-mail and Usenet in order to prepare for the terrorist attacks on September 11. The terrorist training manual “Technological Mujahid, a manual for jihad” contains a chapter on the use of steganography. [17]
In 2010, the Federal Bureau of Investigation discovered that the Foreign Intelligence Service of the Russian Federation used special software to hide information in images. This method was used to communicate with agents without diplomatic cover abroad. [18]
An example of using steganography as Internet art is to embed images in images that appear when they are selected in Internet Explorer, because they highlight images in a certain way when they are selected. [19]
Comments
To leave a comment
Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Cryptography and cryptanalysis, Steganography and Stegoanalysis