Lecture
The use of block cipher for the needs of practical information coding is possible in one of four basic encryption modes (Fig. 2.8):
1) Electronic Code Book (ECB) mode;
2) the cipher block coupling mode (Cipher Block Changing, CBC);
3) ciphertext feedback mode (Electronic Feedback, CFB);
4) output feedback mode (Output Feedback, OFB).
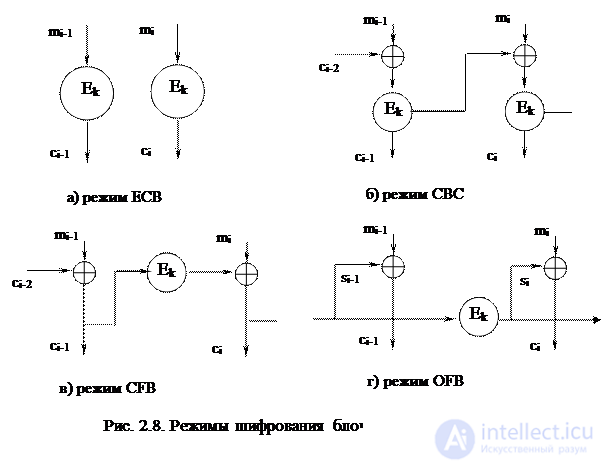 |
In ECB mode, encryption / decryption of the i-th block of plaintext / ciphertext is performed independently of the other blocks:
c i = E k ( m i ) , m i = D k ( c i ) .
The disadvantage of this encryption mode is that identical input text blocks will be encoded into identical ciphertext blocks, which allows an attacker, first, to make assumptions about the nature of the information in the plaintext, and second, to replace one or more ciphertext blocks. The advantage of the regime is the ease of implementation, as well as the possibility of parallelizing the encryption procedure.
CBC mode involves the following encryption / decryption algorithms:
c i = E k ( m i Å c i-1 ) , m i = D k ( c i ) Å c i-1
In CBC mode, each plaintext block is added to the ciphertext block obtained in the previous step. Thus, blocks are linked to each other and independent manipulation with each of them is impossible, and identical input blocks will produce different blocks at the output. However, the task of parallelizing the encoding procedure in this mode is difficult. An additional parameter of encryption / decryption procedures is the c 0 parameter.
In CFB mode, the plaintext block is also “disguised” by encrypted blocks:
c i = m i Å E k ( c i-1 ), m i = D k ( c i-1 ) Å c i
By its capabilities, this mode is similar to CBC mode, but if the message length is not a multiple of the size of the cipher block, then in CBC mode it is necessary to supplement the last block with additional bits and report the true size of the message to the receiving party, and CFB mode allows you to form a ciphertext of the same size as the original message.
In OFB mode, the original message is not subject to crypto-transform at all, it is added to the blocks i encrypted with the secret key (s 0 is a specified non-secret mode parameter):
c i = m i Å s i , m i = c i Å s i , s i = E k ( s i-1 )
In this mode, as in the ECB mode, errors that can occur during the transmission of ciphertext via communication channels are localized in the block, not extending to neighboring ones, and in OFB mode, only the bits that have been changed will be faulty (the whole block will change in ECB). This enables the attacker to substitute a block of ciphertext imperceptibly for the receiving party. The possibility of parallelization of encryption / decryption procedures is difficult.
Comments
To leave a comment
Cryptography and cryptanalysis, Steganography and Stegoanalysis
Terms: Cryptography and cryptanalysis, Steganography and Stegoanalysis