Lecture
I want to say right away that there is no water here about vulnerability, and only the necessary information. In order to better understand what a vulnerability is, I strongly recommend that you read everything from the category Cryptanalysis, Types of Vulnerability and Information Protection
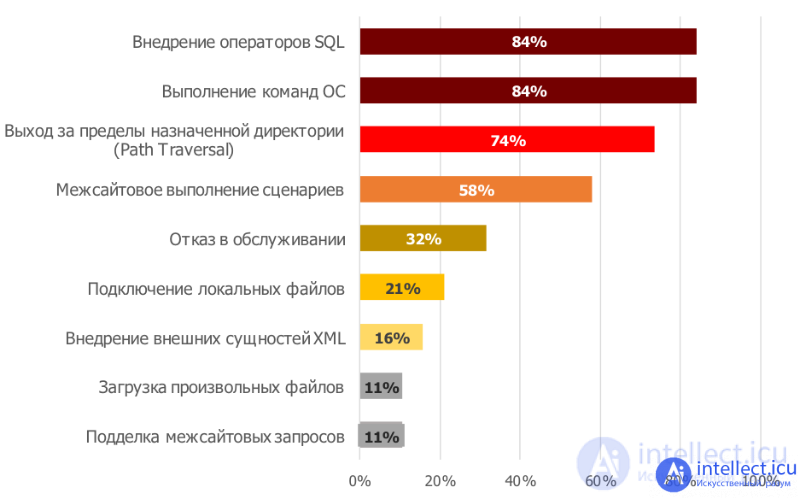
selection of vulnerabilities
1 Brute Force
A method of solving a problem by enumerating all possible options.
The traditional method of dealing with password guessing is limiting the number of mistaken password entries. There are many options for implementing this idea, from the simplest - a static limitation, for example, no more than three errors, to complex dynamic ones, with an increasing prohibition time interval between requests.
2. Insufficient Authentication.
This vulnerability occurs when a Web server allows an attacker to gain access to sensitive information or server functions without proper authentication. Web administration interfaces are a prime example of mission-critical systems.
Depending on the specifics of the application, such components should not be accessible without proper authentication.
The solution is quite simple, when entering the administrative part of the site, the user is obliged to carry out additional authentication, despite the general one on the site.
3. Insecure password recovery (Weak Password Recovery Validation).
This vulnerability occurs when a Web server allows an attacker to unauthorizedly obtain, modify, or recover passwords of other users.
The most effective solution is the following: the user clicks the "Recover password" button and gets to a page where he is asked for his login in the system and the mailbox specified during registration. Next, a notification about the password recovery request and a unique pseudo-randomly generated link to the password change page are sent to the mailbox. In this case, only the owner of the mailbox to which the account is registered can really change the password.
4. The predicted value of the session identifier (Credential / Session Prediction).
Allows to intercept sessions of other users. Such attacks are performed by predicting or guessing the unique identifier of a user's session.
The remedies are to configure the web server correctly, and the safer way is to create your own session mechanism.
5. Lack of authorization (Insufficient Authorization).
Occurs when a Web server allows an attacker to gain access to sensitive information or functionality that should be restricted. Just because a user is authenticated does not mean that they have to access all of the server's functionality and content.
Methods of struggle - a clear delineation of user rights and their capabilities.
6. The site https://intellect.icu says about it. Lack of session timeout (Insufficient Session Expiration).
If a timeout is not provided for the session ID or credentials, or if its value is too large, an attacker can use the old data for authorization.
The method of dealing is simple, limiting the session timeout.
7. Substitution of content (Content Spoofing).
By using this technique, an attacker tricks the user into believing that the pages are generated by the Web server and not sent from an external source.
The error is "childish", that is, to protect against this type of attacks, you just need to stop using frames and, most importantly, never pass absolute or local paths to any files in parameters.
8. Cross-site scripting (Cross-site Scripting, XSS).
The Cross-site Scripting vulnerability allows an attacker to transmit executable code to the server, which will be redirected to the user's browser.
At the moment, the most common type of attack, due to the growing popularity of Web 2.0, the Internet has been filled with various forms of feedback, unfortunately, many of them are not filtered properly, the forms in which some tags or some formatting constructs are allowed are especially difficult. XSS is possible only through careful analysis and filtering of the data that came in requests.
9. Splitting the HTTP request (HTTP Response Splitting).
When this vulnerability is exploited, an attacker sends a specially crafted request to the server, the response to which is interpreted by the target of the attack as two different responses. The second response is completely under the control of the attacker, giving him the ability to spoof the server response.
10. Buffer Overflow.
Buffer overflow exploitation allows an attacker to change the execution path of a program by overwriting data in the system memory. Buffer overflows are the most common cause of program errors.
Thoroughly check the input parameters of CGI scripts written in C ++ or C, and also take care to protect against attacks of this type, this is the timely update of server programs, be it a Web-Server or a DBMS .
11. Attack on the functions of formatting strings (Format String Attack).
When using these attacks, the program execution path is modified by rewriting memory areas using symbolic variable formatting functions. The vulnerability arises when user data is used as arguments to string formatting functions such as fprintf, printf, sprintf, setproctitle, syslog, etc. The
protection is simple - do not use the transmitted data as parameters of these functions, but rather refuse to use these functions due to their potential danger.
12. Execution of OS commands (OS Commanding).
Attacks of this class are aimed at executing operating system commands on a Web server by manipulating input data.
The solution to this problem is a properly configured server.
13. Implementation of SQL statements (SQL Injection).
These attacks target Web servers that issue SQL queries to database servers based on user input.
Another of the most widely exploited types of attacks, means of struggle - competent filtering of the received data.
14. Implementation of server extensions (SSI Injection).
Attacks of this class allow an attacker to transmit executable code, which will later be executed on a Web server. Vulnerabilities leading to the possibility of these attacks usually consist in the failure to validate the data provided by the user before storing it in a file interpreted by the server.
The server can execute scripts before generating the HTML page, such as Server-site Includes (SSI). In some situations, the source code of the pages is generated based on the data provided by the user.
If an attacker transmits SSI statements to the server, the attacker may be able to execute operating system commands or include prohibited content the next time it is displayed.
The opposition is the same as with SQL injection.
15. Indexing directories (Directory Indexing).
Providing a list of files in a directory is normal Web server behavior if the default page (index.html / home.html / default.htm) is not present.
The solution is simple enough - all directories must contain the default page file, at least in the form of a stub, or the appropriate permissions must be set for the directory.
16. Application identification (Web Server / Application Fingerprinting).
Application versioning is used by an attacker to obtain information about the operating systems, Web servers, and browsers used by the server and client. It can also target other components of the Web application, such as a directory service or database server, or underlying programming technologies.
In order to protect against this error, it is necessary to minimize, or it is better to completely exclude the system information given to the user, however, an experienced attacker can analyze and find out the names of the programs used by some specific features of these programs.
17. Information Leakage.
These vulnerabilities arise in situations where the server publishes sensitive information, such as developer comments or error messages, that can be used to compromise the system.
Often, developers leave comments in HTML pages and script code to help find bugs and maintain the application. This information can range from simple descriptions of the details of how the program works, to, in the worst cases, usernames and passwords used in debugging.
18. Return path in directories (Path Traversal).
This attack technique is aimed at gaining access to files, directories and commands outside the main directory of the web server.
The countermeasure is careful tuning web servers, many hosting servers neglect this. From personal experience, we can mark the servers of the AGAVA company, using a special PHP script loaded into your own folder, you can go through the entire server folder tree.
19. Predictable resource location (Predictable Resource Location).
Allows an attacker to gain access to hidden data or functionality. By brute-force attack, an attacker can gain access to content that is not intended for public viewing.
20. Denial of Service.
This class of attacks is aimed at disrupting the availability of a Web server.
A very common type of attacks, the means of protection are optimization code, and, which is more effective if the attacker has some power, the introduction of restrictions on the amount of data sent per unit of time.
21. Insufficient Anti-automation.
Insufficient opposition to automation occurs when the server allows the automatic execution of operations that must be performed manually.
The standard tool for fighting robots is now CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) - a fully automated public Turing test for distinguishing between computers and people.
22. Insufficient Process Validation.
Vulnerabilities of this class arise when the server does not sufficiently check
Directory traversal attack
http://en.wikipedia.org/wiki/Directory_traversal_attack
program for testing vulnerabilities of websites https://subgraph.com/vega/download/
Comments
To leave a comment
Cryptanalysis, Types of Vulnerability and Information Protection
Terms: Cryptanalysis, Types of Vulnerability and Information Protection